Keeping Real Estate Transactions Safe: Cybersecurity Best Practices


Disclaimer: The information provided on this site does not, and is not intended to, constitute legal, financial, tax, or real estate advice. Please consult your expert for advice in those areas. All content is for general informational purposes only and is not intended to provide a complete description of the subject matter. Although Blueprint provides information it believes to be accurate, Blueprint makes no representations or warranties about the accuracy or completeness of the information contained on this site. Specific processes will vary based on applicable law. The title and closing process will be handled by a third-party attorney to the extent required by law. Product offerings vary by jurisdiction and are not available or solicited in any state where we are not licensed.
Technology provides convenient new ways for people to connect and do business, but it also creates new opportunities for cybercriminals to exploit vulnerabilities. The FBI’s Internet Crime Complaint Center (IC3) is an organization for victims of cybercrime to report incidents. It investigates and helps recover assets. To prevent further attacks, it publishes a report on cybercrime activity so the public can understand the latest trends and threats.
The 2021 report shows a significant uptick in phishing, vishing, smishing, and pharming attacks compared to previous years. Email is used by these criminals to complete one of these attacks, and as a result, Business Email Compromise (BEC) continues to be one of the costliest types of fraud, with a total loss of nearly $2.4 billion in 2021.
BEC is a common tactic when targeting real estate transactions, but it’s not the only one. Learn more about how cybercriminals target real estate transactions and the cybersecurity best practices to prevent fraud.
During the pandemic-driven homebuying bonanza, devastating headlines about homebuyers losing their life savings to cybercriminals multiplied. The stories often shared a similar pattern. An eager homebuyer receives an email from what seems to be the title company requesting their down payment to be sent to a new account. Fearing any delay would result in losing their bid on the house, they act quickly. The request seems reasonable and appropriately timed among the flood of paperwork, so they send the money. The homebuyer doesn’t notice any red flags like a misspelled email address, and the money lands in a fraudster’s account.
Real estate transactions attract cybercriminals for several reasons:
- Large sums of money. Down payments or mortgage payoffs can total tens of thousands of dollars and easily reach higher amounts. Meanwhile, the average bank robbery only yields about $1,797.
- Lower effort for higher reward. Compared to other forms of criminal activity, the risk and reward for cybercriminals are tilted in their favor. They may target several transactions and send several emails before one person falls for the scheme, but the payday is massive compared to the effort. Once the money hits the first fraudulent account, it’s quickly drained and moved to cryptocurrency wallets, making recovery efforts difficult.
- Multiple parties mean multiple points of contact to exploit. Homebuyers aren’t the only parties targeted in these wire fraud scams. Title agents, real estate agents, and mortgage professionals are all vulnerable targets.
An American Land Title Association survey reported that title agents identified a wire fraud attempt in a third of all real estate transactions. Fortunately, only 8% of these attempts resulted in funds being wired to a fraudulent account, but a full recovery of funds was possible in only 29% of those cases.
What Tactics Do Cybercriminals Use?
The setup for a wire fraud scam starts well before that email requesting funds is sent. Through phishing, portal spoofing, business email compromise, and social engineering, fraudsters can access communications and sensitive information.
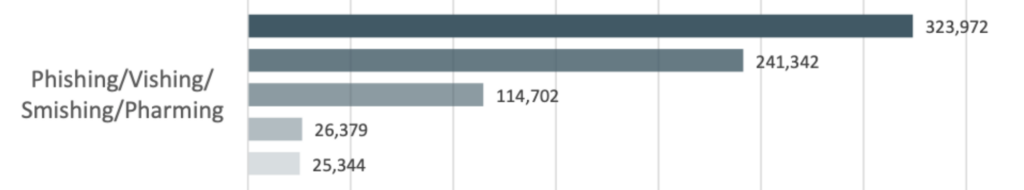
Phishing, Vishing, Smishing, and Pharming
Phishing is a play on the word fishing. A malicious link hidden in a legitimate-looking email acts as “bait” to get the recipient to click. Clicking the link results in either downloading malware to the target’s device or landing on a page with a fake portal to steal credentials like login names and passwords. The term has led to several other spin-off terms denoting the various channels used to trick victims.
Spear phishing is when cybercriminals pose as a leader at a company to manipulate employees to gain access to login credentials or send funds to fraudulent accounts.
Vishing, or voice phishing, is when cybercriminals call their intended target and pose as tech support, a government agency, or another organization to extract sensitive information like a bank account or credit card information.
Smishing involves text messages with malicious links sent to smartphones.
Pharming sends unsuspecting targets to fraudulent websites after the user has downloaded malicious code.
Closing phishing is when a legitimate and previously sent email containing attachments or links is duplicated. The fake email is designed to look like a simple re-send from the original sender and sent to many recipients. Once one of those recipients clicks on the email, the tactic is repeated with the same forged email forwarded to the new victim’s contacts.
Business Email Compromise
Business email compromise, or BEC, continues to be one of the most common types of cybercrime. In 2021, the IC3 reported an estimated $2,395,953,296 in losses.
The tactic uses various phishing methods to target companies that conduct wire transfers and their clients. The fraudsters use social engineering, a form of psychological manipulation, to get unsuspecting victims to perform actions or divulge confidential information. A few common BEC scenarios include:
- Cybercriminals pose as a CEO or executive to pressure an employee to transfer money to a fraudulent account.
- A bogus invoice is sent from a fraudster posing as a supplier or vendor with updated payment information.
- An employee’s email account and device are compromised after clicking a malicious link in an email. Once fraudsters have access to an employee’s account, they can send bogus invoices to contact lists, forward communications to their inbox, block incoming messages, and spy on communications about an upcoming real estate transaction.
Virtual Meetings
The newest emerging cybercrime trend exploits the growing popularity of virtual meetings among remote workers. Once an executive’s or financial director’s email is compromised, a virtual meeting request is sent to employees. On the call, the fraudster inserts a picture of the executive with no audio or a “deep fake” audio sound and claims the audio and video connections aren’t working properly. The fraudster then directs employees to send wire transfers or uses the executive’s compromised email to provide wiring instructions.
Remote Desktop Protocol
Remote Desktop Protocol, or RDP, is a convenient tool for remote workers because it allows an authorized user to connect to another user’s computer or network without physical contact. RDP can be essential for troubleshooting technical issues, accessing organization-related data, and providing a more convenient remote work experience. However, it also creates a new entry point for cybercriminals to exploit and gain access to multiple devices and potentially an organization’s entire network.
Cybersecurity Best Practices
While professionals are trained to spot the red flags of a wire fraud attempt, the lack of everyday exposure to cybersecurity best practices means buyers and sellers are at a heightened risk. Because cybercriminals use so many methods to spy on, gather information, manipulate, and deliver malware to targets, cybersecurity best practices require people to be diligent on multiple fronts.
Phishing emails, Remote Desktop Protocol exploitation, and exploitation of software vulnerabilities remain the top three initial points of infection for ransomware incidents reported to the IC3. With that in mind, here are a few cybersecurity tips.
- Keep your computer and programs up to date. Updates often fix bugs and known vulnerabilities used to gain access to devices and accounts. Set up auto-updates to make it easier to keep your computer up to date. Router firmware should also be regularly updated.
- Password hygiene. Use a variety of passwords that are unique to personal and business accounts. A tool like LastPass can help manage passwords and ensure no repeated passwords are used.
- Use complex passwords and two-factor authentication. Use phrases, numbers, and special characters for all passwords. Enable two-factor authentication on all your business or personal accounts, including social media, whenever possible.
- Be suspicious of links in emails. Before clicking, hold your mouse over a link to look for mismatches between the stated destination and the URL that pops in the lower right corner of your screen or below the link.
- Secure your devices. Lost or stolen devices like mobile phones or laptops can expose sensitive personal information. Be sure to enable password protection to access your devices and financial accounts.
- Use a VPN when connecting to unsecured networks. Deter fraudsters from monitoring your correspondences on public WiFi networks by using a VPN. A common tactic is setting up fake public WiFi networks at a coffee shop, shopping mall, or other populated public locations. Once a user is logged in, the hacker can redirect users to fake sites, steal data from existing conversations, or transfer data. A VPN encrypts your online activity and prevents these “man-in-the-middle” attacks.
- Enhance your email security. Email is not inherently secure. Free email service providers are convenient but may be more vulnerable to cyberattacks. While many free providers use Transport Layer Security (TLS), not all do. Even if TLS is used to deliver emails, it doesn’t mean that the content of emails is private from other parties. For instance, Google encrypts emails with TLS but still scans email content for features like Smart Reply. Additionally, the information is no longer protected in transit if the recipient doesn’t have an email provider that also uses TLS. Review your provider’s security standards and consider upgrading to a provider with end-to-end encryption.
- Read your title company’s wiring instructions. Every title company or real estate law firm will send you specific instructions regarding wire transfers. The bank account will rarely change, so if you receive a notification of updated instructions, proceed with caution. Call a known number to verify if the instructions are legitimate.
Safe Real Estate Transactions with Blueprint
Balancing cybersecurity with convenience is a top priority for the Blueprint team. Our digital platform and internal processes bridge the gap between those extremes. In doing so, Blueprint offers a modern title and closing solution for complex real estate transactions.
First, our entire team follows all of the best practices laid out here in this article. Our IT department enforces software and hardware updates to ensure best-in-class security at the individual level. Our team undergoes regular security compliance training to keep us sharp. We care deeply about our customers, so extreme focus is placed on securely processing all information from our customers and clients.
Secondly, our digital platform is designed from the ground up using security best practices, including encrypted file transfers, time-limited file access, role-based permissions, and need-to-access information restrictions. Our software engineering team leverages modern encrypted cloud technology to provide real-time updates on your transactions’ status and securely conduct transactions through our technology platform. Getting secure updates to your transactions and secure access to the related files has never been easier.
Finally, we rigorously screen third-party tools before adding them to our operation team’s software stack. Everything from email communication providers to file processing tools to notary scheduling software systems is thoroughly vetted to meet encryption and security standards.
Blueprint is dedicated to delivering best-in-class, secure service for real estate professionals who want a modern, digital title and closing experience.
To learn more about Blueprint, schedule a demo today.
